Search results for tag #openbsd
#OpenBSD
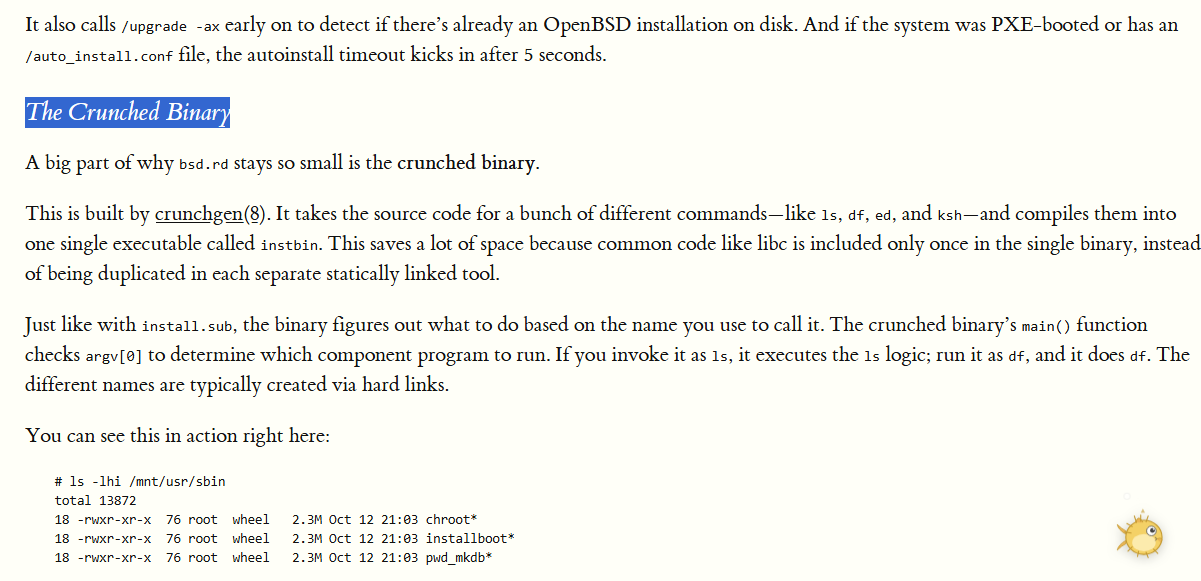
Updated the article about bsd.rd.
Added a section on the crunched binary.
👉 https://www.openbsdjumpstart.org/bsd.rd
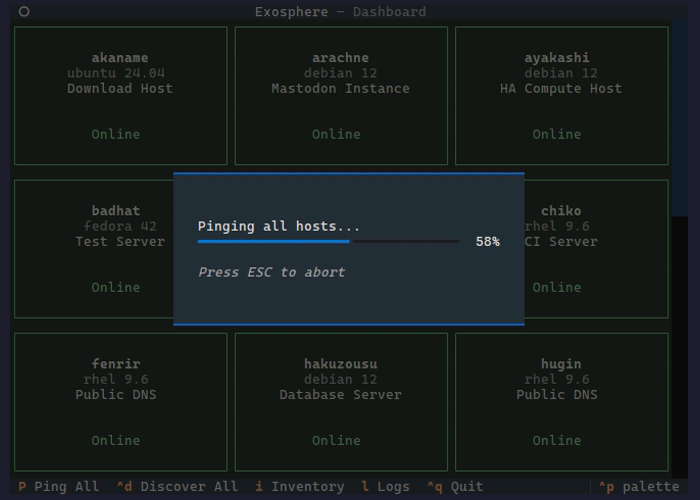
Exosphere:
― aggregated patch and security update reporting
― basic system status across multiple Unix-like hosts via SSH
<https://exosphere.readthedocs.io/> | <https://github.com/mrdaemon/exosphere>
<https://untrusted.website/@mr_daemon/114980024541462116> @mr_daemon
<https://mastodon.social/@terminaltrove/114977286773333343> @terminaltrove
#Unix #Linux #BSD #FreeBSD #OpenBSD #Debian #Ubuntu #RedHat #macOS #Windows #SSH
Anatomy of bsd.rd
https://openbsdjumpstart.org/bsd.rd/
"Todo administrador de OpenBSD ha arrancado bsd.rd al menos una vez, para instalar, actualizar o rescatar un sistema dañado. Pero pocos se detienen a mirar qué contiene realmente ese archivo. Resulta que bsd.rd es un conjunto de capas anidadas, y se puede desmontar en un sistema en ejecución sin reiniciar nada."
del autor de OpenBSD jumpstart (Wesley)
#OpenBSD 🐡
Good news about our financial situation: The Game of Trees Hub (https://gothub.org) is no longer operating at a loss 
With two business subscriptions booked yesterday (from Ireland  ) we are now making more money than we are spending.
) we are now making more money than we are spending.
Our average monthly expenses are currently 393€. We are now receiving 243€ monthly from active subscribers. Additionally, we are currently receiving 220€ per month from generous people who support us on https://opencollective.com/gothub
Ever since we started renting servers back in May 2025 our funds had been slowly depleting because the monthly bills from hosting providers exceeded our monthly income. Fortunately, we could sustain this situation for a while because of a reserve built up from generous contributions on Open Collective since June 2024. We are very grateful to all of you who are helping to make our project possible.
Our friends from https://openbsdjumpstart.org published a nice article about bsd.rd.
Lab: Anatomy of bsd.rd — No Reboot Required
Right now I'm testing #OpenBSD 7.8 on the #framework laptop (Framework Laptop 13 DIY Edition (AMD Ryzen™ AI 300 Series)).
Everything works until it doesn't. Sometimes when display content changes fast (activating screensaver or opening browser full screen) the system freezes completely without any error message. Any ideas to see what's happening ?
I just wrapped up an interesting call that was originally scheduled for last week but rescheduled for today. The client is looking for a unique setup, and thanks to having an early re-read of the fantastic The Book of PF - 4th Edition, I was able to propose some configurations that had completely slipped my mind. The client is extremely curious, and this will likely lead to a new OpenBSD deployment in an interesting environment.
At the same time, I received an email from a professor at an Italian university whom I had encouraged to extend his lectures to include BSDs. I piqued his curiosity as well and proposed a session specifically on firewalls, focusing on OpenBSD and pf. He will be reading The Book of PF soon and will likely add it to his students' recommended reading list. I'll probably present them, too.
In short - one book, a thousand new possibilities. Infinite thanks to @pitrh for the massive and wonderful work behind it.
https://nostarch.com/book-of-pf-4th-edition
#OpenBSD #FreeBSD #NetBSD #RunBSD #PF #Firewalling #IT #SysAdmin
Latest 𝗩𝗮𝗹𝘂𝗮𝗯𝗹𝗲 𝗡𝗲𝘄𝘀 - 𝟮𝟬𝟮𝟲/𝟬𝟮/𝟭𝟲 (Valuable News - 2026/02/16) available.
https://vermaden.wordpress.com/2026/02/16/valuable-news-2026-02-16/
Past releases: https://vermaden.wordpress.com/news/
#verblog #vernews #news #bsd #freebsd #openbsd #netbsd #linux #unix #zfs #opnsense #ghostbsd #solaris #vermadenday
Is it monday morning already? Then I guess it's time for the next episode of the #OpenBSD on sgi story.
Still bleak at this point. Stay tuned for the next episode when the fun really starts!
We have spun up 5 new VMs during the last 48 hours. Some were booked by known friends of ours, some booked by new friends we have never met before. Welcome on board!
Does anyone know if #OpenBSD 7.7 can be upgraded to 7.8 on Apple Silicon, or if 7.8 can be coaxed into installing fresh? There appears to be a regression.
Happy #ilovefs day, everyone!
A huge thank you to all the amazing free software community members who build and distribute the software we use everyday.
A special thank you (because I like and use these projects) to the Xfce team, the GrapheneOS developers, the Fedora and openSUSE community, the LibreOffice community, and the wonderful people behind the BSDs.
On another year of awesome free and open source software.
#opensource #freesoftware #linux #bsd #fedora #opensuse #archlinux #gentoo #voidlinux #debian #ubuntu #freebsd #openbsd #netbsd #almalinux #rockylinux #libreoffice #grapheneos #xfce #gnome #kdeplasma #lxqt
The fresh 4th edition of The Book of PF in physical form has reached Europe (Ireland), https://www.linkedin.com/posts/tomsmythconnect_thebookofpf-openbsd-packetfilter-activity-7427686906349555713-7s4w - so my stack of author copies are hopefully on the way too.
The book home page is at https://nostarch.com/book-of-pf-4th-edition
Some background https://nxdomain.no/~peter/yes_the_book_of_pf_4th_ed_is_coming.html @nostarch #bookofpf #openbsd #freebsd #pf #packetfilter #networking #security
Was trying out Game of Trees and more specifically gotwebd [https://gameoftrees.org/gotwebd.8.html] the other day and LOVED it. So simple to whip up via httpd. Tiny and easy to digest configs. Was able to toss some things over from certain other proprietary repo hosting without any sweat or issue.
Looks like they just had a recent release too: https://www.undeadly.org/cgi?action=article;sid=20260211061627
#OpenBSD
Game of Trees 0.122 released https://www.undeadly.org/cgi?action=article;sid=20260211061627 #openbsd #got #git #gameoftrees #versioncontrol #development #freesoftware #libresoftware
All our hosted Git repository servers have been updated to today's new 0.122 release of the Git-compatible #gameoftrees version control system.
This update brings fixes and tweaks for the web frontend. In particular, #OpenSSH host key fingerprints are now prominently displayed where it matters, encouraging users to verify host keys instead of trusting them blindly on first use. See the Game of Trees change log for details: https://gameoftrees.org/releases/changes.html#2026-02-10
We anticipate upcoming support for SHA256 object-format Git repositories, hopefully in the next release (as per https://bsd.network/@op/116030524380288866)
By the way, we still have spare room for more hosted VMs. If you want some no-nonsense, community-driven, minimal #git repository and static website hosting in your life then find us at https://gothub.org/
Our service runs #OpenBSD exclusively but no expertise in BSD is required at all to make use of it. Repositories, user accounts, access rules, commit notifications, and web hosting can be managed by editing a plain-text configuration file stored in a Git repository.
The latest Valuable News by @vermaden https://vermaden.wordpress.com/2026/02/09/valuable-news-2026-02-09/ notes that The Book of PF, 4th edition https://nostarch.com/book-of-pf-4th-edition has been released #bookofpf #openbsd #freebsd #networking #pf @nostarch
Latest 𝗩𝗮𝗹𝘂𝗮𝗯𝗹𝗲 𝗡𝗲𝘄𝘀 - 𝟮𝟬𝟮𝟲/𝟬𝟮/𝟬𝟵 (Valuable News - 2026/02/09) available.
https://vermaden.wordpress.com/2026/02/09/valuable-news-2026-02-09/
Past releases: https://vermaden.wordpress.com/news/
#verblog #vernews #news #bsd #freebsd #openbsd #netbsd #linux #unix #zfs #opnsense #ghostbsd #solaris #vermadenday
Upcoming "Network Management with the OpenBSD Packet Filter Toolset" tutorials (covering #freebsd and #openbsd):
2026-03-19 AsiaBSDCob https://www.asiabsdcon.org
2026-06-18 BSDCan https://www.bsdcan.org
See https://nxdomain.no/~peter/pf_tutorial_upcoming_questions_welcome.html (https://bsdly.blogspot.com/2025/05/for-upcoming-pf-tutorials-we-welcome.html)
and https://nxdomain.no/~peter/what_is_bsd_come_to_a_conference_to_find_out.html (https://bsdly.blogspot.com/2025/11/what-is-bsd-come-to-conference-to-find.html)
plus https://nxdomain.no/~peter/yes_the_book_of_pf_4th_ed_is_coming.html (https://bsdly.blogspot.com/2025/07/yes-book-of-pf-4th-edition-is-coming.html)
Registration for BSDCan 2026 is open at https://www.bsdcan.org/2026/registration.html + tutorial schedule published.
#bsdcan #freebsd #openbsd #netbsd #development #networking #devops #sysadmin #conferences
For more on BSD and the BSD conferences, see https://nxdomain.no/~peter/what_is_bsd_come_to_a_conference_to_find_out.html (or tracked https://bsdly.blogspot.com/2025/11/what-is-bsd-come-to-conference-to-find.html +
https://medium.com/@peter.hansteen/what-is-bsd-come-to-a-conference-to-find-out-06acd7d77fd8 )
Hey #OpenBSD cool kids!
I like how this tool creates OpenBSD virtual machine images with a mix of a local mirror, signify, and QEMU, but it does not support EFI images, raw images, and is, while not fatal, in BASH.
https://github.com/hcartiaux/openbsd-cloud-image
Do you have any tools that check the above checkboxes?
❤️
Newsflash: we have a date for BSD-NL, for the Early 2026 day-conference. Go follow @bsd_nl to get the announcement straight into your timeline 
#BSDNL #BSD #OpenBSD #HardenedBSD #FreeBSD #SecBSD #NetBSD #RUNBSD #MyMotherRunsBSD
Registration for BSDCan 2026 is now open https://www.bsdcan.org/2026/registration.html and tutorials schedule is published.
#bsdcan #openbsd #netbsd #freebsd #libresoftware #freesoftware #conference #development #networking #sysadmin #devops
"The Rest Is Trash"
We are now halfway through the nineteenth year of greytrapping, still tracking and collecting from the wealth of imbecility out there
https://nxdomain.no/~peter/the_rest_is_trash.html (tracked https://bsdly.blogspot.com/2026/02/the-rest-is-trash.html) #spamd #greytrapping #greylisting #openbsd #freebsd #spam #antispam #cybercrime
I added a few more translations of the phrase "This is trash" to the spamtraps at https://nxdomain.no/~peter/traplist.shtml (see https://nxdomain.no/~peter/the_rest_is_trash.html or https://bsdly.blogspot.com/2026/02/the-rest-is-trash.html).
If you want further translations added, please let me know (with translation in your message).
#spamtraps #greytrapping #spamd #openbsd #freebsd #antispam #imaginaryfriends #localization #cybercrime
The list without wrapper text is available as https://www.bsdly.net/~peter/sortlist.txt (BIG! -- 22975800 entries as of right now, will increase)
Just a shout out to everyone directly or loosly involved in *BSD world here on fedi and elsewhere.
Thanks for having me here. It's been a couple of years now since I migrated from Linux and really enjoying it.
be safe and keep up the excellent work,
#appreciation #bsd #kiss #unix #freebsd #openbsd #netbsd #dragonfly #runbsd #illumos
acquired - tome of pf
(this is not sponsored content, I just like the book)
thank you @pitrh
last of the fish
#unix_surrealism #technomage #gameoftrees #9front no #thinkpad #openbsd #runbsd
Static Web Hosting on the Intel N150: FreeBSD, SmartOS, NetBSD, OpenBSD and Linux Compared
Update: This post has been updated to include Docker benchmarks and a comparison of container overhead versus FreeBSD Jails and illumos Zones.
#ITNotes #freebsd #illumos #jail #linux #netbsd #openbsd #ownyourdata #server #smartos #sysadmin #zoneshosting
This Isn't a Battle
After reading a post describing the FreeBSD community as 'toxic', I share a different perspective. This isn't a battle. It's a reflection on coexistence, the original Open Source spirit, and the quiet richness of taking a different path.
https://my-notes.dragas.net/2025/11/14/this-isnt-a-battle/
#MyNotes #IT #SysAdmin #FreeBSD #NetBSD #OpenBSD #Linux #OpenSource
bathing
I use @OpenBSDAms btw
#unix_surrealism #openbsd #vmm #vmd #poster #comic #linux #plan9 #glenda
rio-like configuration for base openbsd fvwm2
Prehistoric AI, OpenBlade's relative
#unix_surrealism #lispmachine #openblade #openbsd #technomage #comic
Heads up for people applying the first syspatch(8) for #OpenBSD 7.8, which is actually for the syspatch(8) utility itself.
There are instructions in the errata patch for if it fails.
If syspatch fails (probably because /usr is not a separate filesystem), perform these steps:
sed -e 's/.checkfs/#checkfs/g' /usr/sbin/syspatch > /root/syspatch
ksh /root/syspatch
syspatch # re-run new syspatch command as instructed
rm /root/syspatch
dev_mkdb
Thanks to everyone involved. All hail the fish.
The Man of MATA pt1
next: https://merveilles.town/@prahou/115271822786360293
pls consider supporting my work: https://analognowhere.com/support
#unix_surrealism #comic #technomage #openbsd #linux #penguin #mata
Me: huh, I don't remember logging out of my session on the kids' #OpenBSD laptop…oh, right, I did a `doas sysupgrade`, it did the upgrade, rebooted into 7.7, and returned uneventfully to the login screen without requiring any additional intervention or thought.
There's something wonderful about an upgrade-process so boring that you can accidentally forget you did it.
I got asked if I could create a #howto for creating a (public) #NAT64 service - just like I did recently for #BoxyBSD. With #DNS64 and #NAT64 you can also reach resource in the legacy internet (#IPv4) on #IPv6 only systems.
While this is based on #unbound and #tayga, there’s also a solution by using the #OpenBSD's native way which is also running on the other gateway. I’ll share a second how to how to do this in OpenBSD and pf.
https://gyptazy.com/howto-create-a-public-dns64-nat64-gateway/
While I was mucking about with an #openbsd port, I got an email from github offering me access to their ai code writing uselessness.
No! Bad website!
*spritzes with water bottle*
My code doesn't work at the moment. Broken is still better than this offer.
This is my favorite part of the OpenBSD installer because I get it wrong every time, but I love that they anticipated it! #openbsd
**BSD Mail Project Update!**
Hello everyone! I wanted to share some exciting updates about the development of BSD Mail, our privacy-focused email service designed with robustness, security, and transparency in mind. Here’s a deep dive into the technical choices I've made, focusing on my use of open source solutions and open protocols:
🌍 **Servers & Location**
- We're running on two physical servers:
- One hosted by OVH in France
- Another by Hetzner in Germany
- Both servers operate on FreeBSD with NVMe drives in a ZFS mirror configuration for speed and data integrity.
🔒 **Virtualization & Security**
- We utilize jails on both servers to ensure isolated environments for different services, managed via BastilleBSD. On one server, jails are set up directly on the hardware, whereas the other server employs nested jails.
- Each server hosts a bhyve VM running OpenBSD with OpenSMTPD for handling SMTP duties securely.
🔗 **Networking**
- A Wireguard setup connects the two servers, facilitating routing capabilities so that jails and VMs can communicate seamlessly, supporting both IPv4 and IPv6.
📧 **Email Services**
- **Dovecot** is configured for maildir replication across the servers using Dovecot sync, ensuring email availability and redundancy.
- **Rspamd** instances are tied to local KeyDB jails, set up in master-master replication for consistent and reliable spam detection and greylisting.
- **ClamAV** runs in corresponding jails for virus scanning, maintaining a high level of security.
- **SOGo** provides a web interface for email management, connected to MySQL databases in master-master replication to handle sessions and authentication smoothly.
💾 **Data Management**
- Email data is stored on separate, encrypted ZFS datasets to secure emails at rest.
- MySQL databases are used for storing credentials and managing sessions for SOGo, also in a master-master replication setup. Importantly, all passwords are securely hashed using bcrypt, ensuring they are salted and safe.
🔎 **Monitoring & Reliability**
- Our DNS is managed through BunnyNet, which continuously monitors our server status. Should one server—or a specific service—become unavailable, DNS configurations are dynamically adjusted to avoid directing users to the affected IP until full service is restored.
🌐 **Commitment to Open Source and Open Protocols**
- Every component of BSD Mail is built exclusively using open source software and open protocols. This commitment is crucial for ensuring data freedom and the reliability of the solutions we use.
This setup not only emphasizes our commitment to privacy and security but also our dedication to maintaining an open and transparent platform.
We're excited to bring you a service where your privacy, data integrity, and freedom are prioritized. Stay tuned for more updates!
#BSDMail #OpenSource #Privacy #FreeBSD #OpenBSD #EmailHosting #Email








 [
[














![[?]](https://triptico.com/social/angel/s/4489c37d896224fc004b7759f2960515.jpg)







